Cybersecurity is an ever-evolving battleground where hackers and defenders continuously outmaneuver each other. Recent incidents involving the Lazarus hacking group, the stealthy cryptojacking of AWS credentials, and a critical Apache ActiveMQ flaw highlight the complexities of this digital warfare.
Lazarus hackers breached dev repeatedly to deploy SIGNBT malware
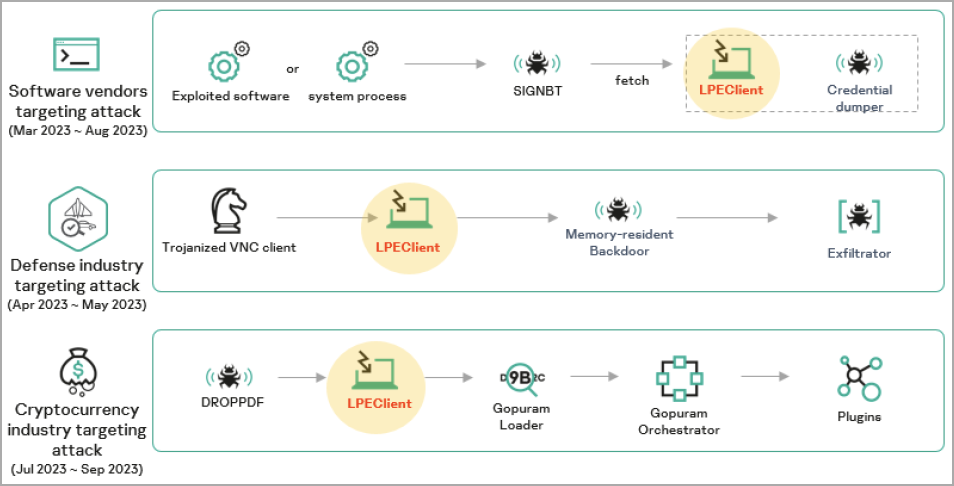
An alarming pattern of breaches has come to light involving the notorious Lazarus group, a North Korean state-sponsored hacking collective. According to a detailed analysis by Kaspersky, the group has managed to repeatedly infiltrate a software vendor, exploiting weaknesses in the vendor’s software—despite patches and security advisories being issued.
These intrusions continue unabated despite the implementation of patches and the issuance of security advisories. The recurrent nature of these breaches points towards a concerted effort to expropriate critical source code or to subvert the software supply chain, thus posing substantial concerns regarding the efficacy of current cybersecurity measures and the necessity for preemptive strategies.
The Lazarus group has employed a sophisticated strand of malware, termed SIGNBT, which exhibits formidable capabilities in evasion, allowing it to conduct a plethora of malicious undertakings including the theft of data and the further propagation of malware. This incident serves as a salient reminder of the perpetually evolving landscape of cyber threats and reinforces the perpetual need for vigilance within the cybersecurity sector.
Cryptojackers steal AWS credentials from GitHub in 5 minutes
Cybersecurity experts from Palo Alto Networks’s Unit 42 has recently uncovered a startling cybersecurity breach, which they’ve named “EleKtra-Leak.” It appears that certain GitHub repositories have been compromised, with the attackers quickly hijacking AWS credentials.
What’s more, within five minutes of gaining access, these individuals have been deploying Amazon EC2 instances to mine the Monero cryptocurrency. This scheme, active since at least 2020, has shown remarkable efficiency, with the attackers automating their attacks through more than 400 API calls in under seven minutes.
Despite GitHub’s proactive secret scanning and AWS’s stringent security measures, these cybercriminals have cleverly navigated around such defenses. This incident highlights the craftiness of modern cybercriminals and emphasizes the absolute necessity for organizations to adopt independent security measures in their CI/CD pipelines, such as scanning repositories upon each commit to prevent such breaches. The continued sophistication of these attacks underscores the ongoing battle between cybersecurity measures and the ingenuity of hackers.
Apache ActiveMQ and the Vulnerability Exploit
A critical vulnerability in Apache ActiveMQ, identified as CVE-2023-46604, has been targeted by ransomware criminals. The flaw, which permits unauthorized remote code execution, became public knowledge on October 25. Even though solutions to this issue were quickly provided, the security enterprise Rapid7 found that two of its clientele suffered ransomware attacks from the HelloKitty faction, despite the existence of a patch.
Moreover, investigations by Shadowserver indicated that an alarming quantity of services had not implemented the fix, with a considerable number of these susceptible services situated in China.
Protect your applications from security vulnerabilities with MergeBase
In today’s high-stakes cyber environment, staying ahead of potential software security breaches is paramount. Effective and swift patch management acts as a vital shield against such digital threats. Being informed about existing vulnerabilities and consistently applying updates is crucial for a robust defense.
MergeBase is a strong ally in these efforts, delivering immediate insights and streamlining the patch application process to minimize the risk window for potential attackers decisively.

