OpenSSL has classified an upcoming issue as critical severity as it affects common configurations and can be exploited (CVE-2022-3602). So far (it’s October 31st right now as I type this blog post), they are not saying anything else.
It is mostly a Linux package, so here is what you should do tomorrow:
- Ubuntu/Debian users should run “apt update” and “apt upgrade,”
- Redhat/Amazon/Fedora/Suse users should run “yum update,”
- Alpine users should run “apk update” and “apk upgrade.”
- Any Docker containers running on base images based on any of the above obviously need to be re-imaged!
- Typically updates do not require machine restarts, but personally, I would still reboot.
Also, after upgrading, everyone should then type “openssl version” on their machines to verify whether they even have it installed and are running a vulnerable version.
For example, on my machine right now (Ubuntu 22.04 – October 31st – 1 day before the security release):
$ openssl version
OpenSSL 3.0.2 15 Mar 2022 (Library: OpenSSL 3.0.2 15 Mar 2022)
Yikes! I’m vulnerable!
But seeing as it’s still Monday, October 31st, there is not much I can else I can do at this point.
Note: Only versions 3.x before 3.0.7 are vulnerable. They have never released any 2.x versions, and versions that start with 1.x are not vulnerable to this bug.
(For now, let’s pray it’s a runtime weakness in OpenSSL, and not a weakness in private keys generated by it since a weakness in generated keys would be a huge headache to deal with – I don’t think keys even retain which version of OpenSSL they were generated by!)
Forthcoming Releases
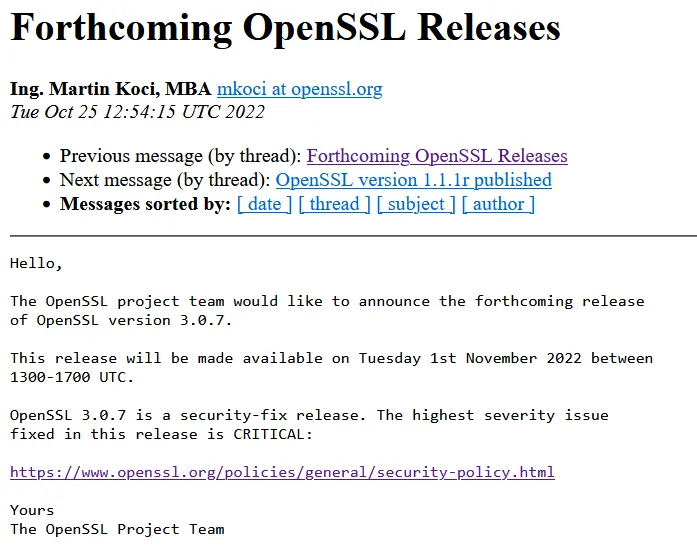
Screenshot from SSL mailing list: CRITICAL bug fix in 3.0.7
More updates after the release on Nov 1st:
- OpenSSL team’s blog post about why they downgraded the vulnerability from CRITICAL to just HIGH.
- AWS Distinguished Engineer Colm MacCárthaigh shows in deep technical detail exactly how the bug works (and how very difficult it would be to exploit).
- Cybersecurity and Infrastructure Security Agency also warn about the vulnerability and encourages users and administrators to review and update to the new version.
Ready to mitigate risks?
Get started for free today or contact us for a demo and find out what MergeBase can do for you!

