Open source licenses grant users permission to use, modify, and distribute software under specific terms and conditions. As the name suggests, the licenses ensure the software’s source code is available to the public. The accessibility of the licenses allows anyone to inspect, modify, and improve the open-source code; however, it also leaves it open to vulnerabilities.
Common vulnerabilities in open source code
The most common open source software vulnerabilities fall into four categories.
- Buffer overflows — These vulnerabilities occur when a program writes more data to a buffer than it can hold, leading to memory corruption and potential exploitation.
- SQL injections — This open source software vulnerability allows attackers to execute malicious SQL (structured query language) queries by injecting code into input fields, potentially leading to unauthorized data access or modification.
- Cross-site scripting (XSS) — This vulnerability enables attackers to inject malicious scripts into web applications, leading to the execution of unauthorized actions in users’ browsers.
- Insecure dependencies — These arise when open-source projects use outdated or vulnerable third-party libraries or frameworks, exposing them to known security flaws.
Examples of notable open source software vulnerabilities
Notable examples of open source software vulnerabilities include
- Heartbleed: A critical security vulnerability in the OpenSSL cryptography library that allowed attackers to read sensitive data from the server’s memory. (Disclosed in 2014)
- Shellshock: A vulnerability in the Bash shell that allowed attackers to execute arbitrary commands on vulnerable systems. (Disclosed in 2014)
- Apache Struts Exploits: Multiple vulnerabilities in the Apache Struts framework have been exploited over the years. Perhaps the most famous is the 2017 Equifax data breach that exposed 147 million people’s personal information.
How to identify vulnerabilities in open source code
Unaddressed open source software vulnerabilities can have significant impacts on a business and its customers. These include data breaches and privacy violations, service disruptions, financial losses due to remediation costs, legal liabilities, loss of revenue, and reputation damage.
This is why it’s essential to know how to identify vulnerabilities in open source code. That way, you can take steps to address them before they become a larger issue. Here are three ways to do it.
Manual code review
A manual code review is a time-consuming and meticulous process that involves a human inspecting the source code to identify potential vulnerabilities, errors, and code quality issues. Developers examine each line of code for logic flaws, insecure coding practices, and deviations from secure coding guidelines.
The reviewer must have expertise in programming languages and security principles and know of common vulnerabilities such as injection flaws, insecure cryptographic practices, and authentication issues.
While there is greater room for error, a manual code review remains a crucial component of comprehensive security assurance for software applications because it allows for a contextual understanding of the codebase. This contextual understanding enables reviewers to identify subtle vulnerabilities automated tools might overlook.
Static analysis
Static analysis focuses on identifying vulnerabilities and quality issues through code inspection, employing various techniques, including data flow analysis, control flow analysis, and abstract interpretation. The key differentiator is static analysis examines source code or compiled binaries without executing them.
By analyzing code at rest, static analysis tools can uncover vulnerabilities early in the development process, allowing developers to address issues before they manifest in runtime environments.
The tools analyze code syntax, structure, and semantics, applying predefined rules, heuristics, and algorithms to detect potential security weaknesses.
Automated source code analysis tools
Automated scanning tools provide a systematic approach to identifying source code vulnerabilities, making for a more efficient and scalable vulnerability detection process.
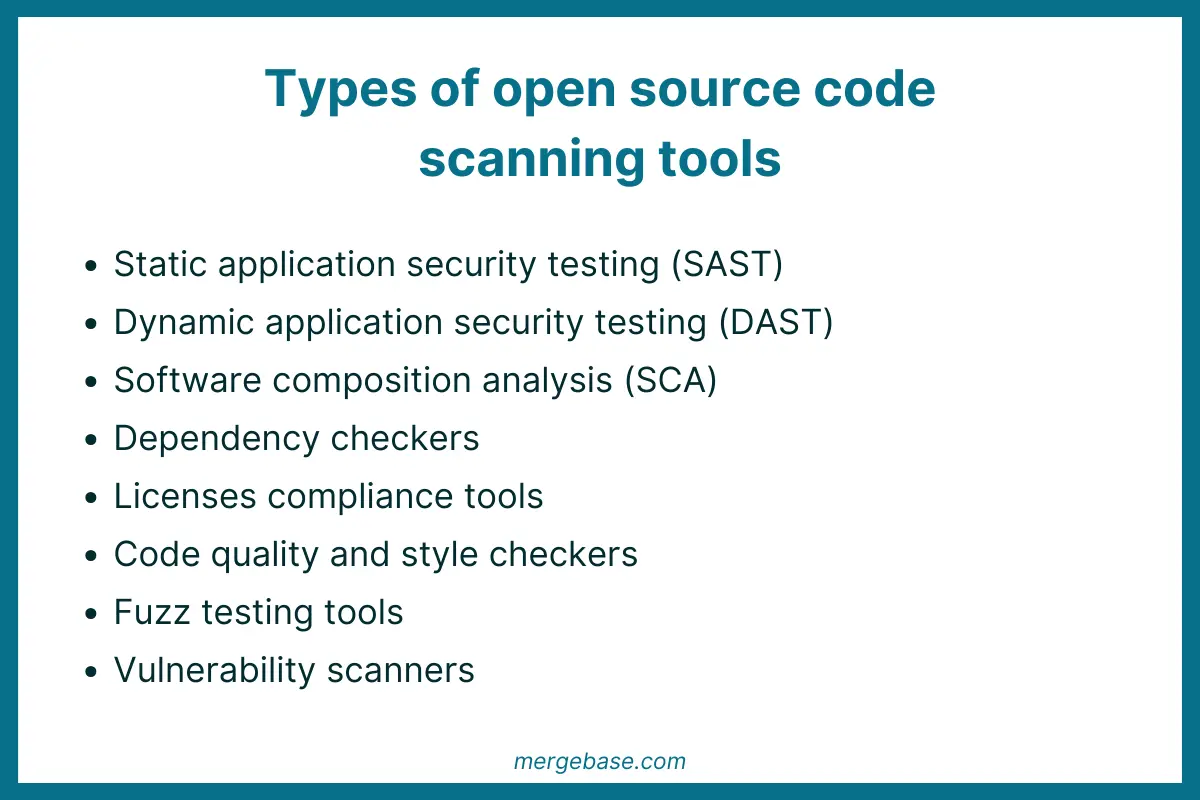
Types of automated scanning tools include
- Software compostion analysis tools that identify open-source components and their dependencies within a codebase. The tools detect outdated libraries, known vulnerabilities in dependencies, and licensing issues.
- Static analysis tools that analyze source code without executing it, searching for patterns indicative of vulnerabilities, such as unsafe function calls, input validation flaws, and insecure configurations.
- Dynamic analysis tools that interact with running software to identify vulnerabilities, including input validation errors, authentication weaknesses, and runtime memory corruption issues.
- Dependency checkers that scan software dependencies for known vulnerabilities and outdated components, helping developers identify and address security risks stemming from third-party libraries and frameworks.
Automated scanning tools are easy to integrate into the software development lifecycle, facilitating continuous vulnerability assessment. The tools enable early detection and the remediation of security issues without requiring much human input.
Conclusion
Whether approaching it manually or using tools to help identify vulnerabilities in your open-source code, implementing a vulnerability detection process into your software development lifecycle is essential. Your proactive approach will help protect the organization from data breaches, privacy violations, service disruptions, and financial losses and ensure your customer data remains secure.
Looking to identify vulnerabilities in your open source code? Scan for free with MergeBase.
MergeBase’s complete software supply chain security solution offers real-time DevSecOps visibility of third-party risk from development into operation, covering all major languages from C/C++, .NET, JavaScript/NPM to Java.
Try it for free and get access to our lowest false positive SCA scanner, patented Java Runtime Protection, and comprehensive SBOM engine. Start your trial and identify the vulnerabilities lurking in your open source code today.