Java has more vulnerabilities than any other programming language combined; it’s also one of the most popular.
Used in core systems that form the backbone of organizations across the globe, Java plays a key role in maintaining critical infrastructure. This makes ensuring robust security measures essential.
While multiple threats impact Java security, this article will focus on just two: insider threats and social engineering.
What is an insider threat?
As the name suggests, insider threats originate within organizations. CISA defines them as “the threat that an insider will use their authorized access, intentionally or unintentionally, to do harm to the department’s mission, resources, personnel, facilities, information, equipment, networks, or systems.”
Insider threats manifest in various ways, including violence, espionage, sabotage, theft, and cyber acts. Yet, while they pose a significant risk to Java security, organizations often underestimate them.
Types of insider threats
Broadly, insider threats can be divided into two categories.
- Malicious insider threats
- Negligent insider threats
In Java security, malicious insider threats are deliberate attempts by individuals within an organization to alter or otherwise interfere with code to disrupt production, derail projects, or leave software vulnerable to future attacks.
Negligent insider threats result when individuals inadvertently compromise security protocols, like opening spurious links or leaving devices out in public places. As a result, Java security defenses are weakened, leaving the door open for threat actors to strike. This type of Java security threat usually arises when organizations don’t have clear, robust security protocols or don’t invest in security awareness training for their employees.
What is social engineering?
Social engineering is becoming more common as businesses deploy more advanced software supply chain security methods because it exploits human psychology rather than technical loopholes.
Social engineering involves employing deceptive or manipulative tactics to coerce unsuspecting victims into performing specific actions. In the broader context of cybercrime, it often involves giving up personal information or sending money. However, within the realm of Java security, social engineering tactics are often used to gain access to the victim’s system.
Common social engineering tactics
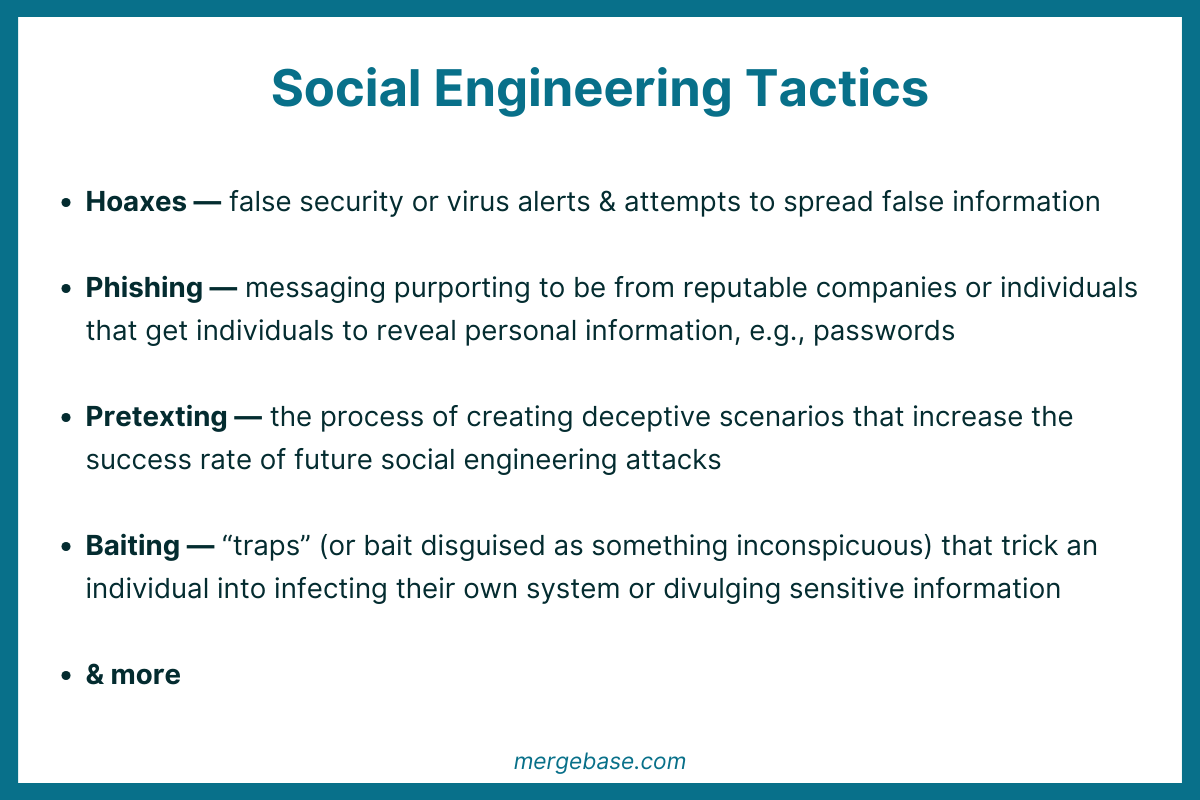
Common social engineering tactics include
- Hoaxes — these often take the form of false security or virus alerts or attempts to spread false information
- Phishing — the fraudulent practice of sending messaging purporting to be from reputable companies or individuals to get individuals to reveal personal information, e.g., passwords
- Pretexting — the process of creating deceptive scenarios that increase the success rate of future social engineering attacks
- Baiting — the process of using a “trap” or bait disguised as something inconspicuous to trick an individual into infecting their own system or divulging sensitive information
- And more
How to recognize insider threats and social engineering
Insider threat indicators
Identifying insider threats within the Java development environment involves a combination of proactive monitoring, observation, and contextual awareness. By leveraging robust access controls and logging mechanisms, development teams can detect abnormal activities early on, mitigating potential risks before they escalate.
When monitoring access patterns and permissions, look out for
- Unauthorized attempts to access sensitive information
- Irregular login times
- Unusual IP locations that don’t align with employee locations
- Requests of additional privileges not required to perform a task
It’s also important to monitor for poor performance appraisals, disciplinary actions, or disagreements with policies, management, etc., which could indicate employee dissatisfaction. As insider threats result from individuals within an organization, monitoring employee satisfaction could highlight disgruntled employees who are at higher risk of carrying out attacks.
Social engineering indicators
To successfully identify social engineering attempts within your Java development environment, you must understand human psychology and be aware of different social engineering tactics.
Indicators of social engineering to look out for (and encourage employees to be suspicious of) include
- Attempts to fabricate scenarios or personas to manipulate individuals into divulging confidential data. For example, an email from a manager requesting files or information be sent to a personal email because they’re having trouble logging into their company one.
- Attempts to create a false sense of urgency
- Attempts to create false credibility by feigning authority
- Unsolicited emails requesting information or containing attachments
- Generic greetings and signatures
- Typos or grammatical errors and inconsistencies in logos or formats
- Email addresses that don’t follow an organization’s typical pattern, e.g., J.Smith@company.com, or have a different address to the sender’s name.
How to protect against Insider Threats and Social Engineering
Mitigating insider threats and social engineering attacks requires a multifaceted approach that combines technological solutions, proactive measures, and a heightened awareness of potential risks.
Robust access controls and monitoring systems are the cornerstone of defense against insider threats. By implementing granular access controls that limit privileges based on job roles and responsibilities, organizations can reduce the likelihood of unauthorized access to sensitive data or systems. Furthermore, continuous monitoring of user activities, network traffic, and system logs enables the timely detection of anomalous behavior, allowing for swift intervention to mitigate potential security breaches.
Equally important is implementing security awareness training programs tailored specifically for Java developers. These training sessions should emphasize the technical aspects of cybersecurity and the recognition and response to potential insider threats and social engineering tactics.
By educating developers about common attack vectors, deceptive tactics used by social engineers, and the importance of adhering to security protocols, organizations can empower their workforce to become proactive guardians of digital assets. Regular training sessions, supplemented by simulated phishing exercises and real-world case studies, help reinforce best practices and foster a culture of security consciousness within the development community.
While technology plays a vital role in safeguarding against insider threats and social engineering tactics, it is essential to recognize that no single solution can provide foolproof protection. Access controls and encryption technologies help fortify digital perimeters and protect sensitive data from unauthorized access or interception. However, the efficacy of these measures is contingent upon human factors such as adherence to security policies and awareness of potential risks. Therefore, a holistic approach that addresses technical and human factors is imperative. This entails cultivating a security-centric organizational culture, promoting open communication channels for reporting suspicious activities and fostering a sense of collective responsibility for maintaining cybersecurity resilience.
Furthermore, encryption technologies, such as end-to-end encryption and data-at-rest encryption, help mitigate the risk of data breaches by rendering intercepted information unreadable to unauthorized parties. Implementing multi-factor authentication (MFA) mechanisms adds an extra layer of security, making it significantly harder for adversaries to gain unauthorized access even if login credentials are compromised. However, balancing security measures and user experience is crucial to avoid impeding productivity and usability.
Conclusion
In conclusion, safeguarding Java applications against insider threats and social engineering attacks is imperative in today’s digital landscape. Organizations can significantly enhance their cybersecurity posture by understanding the nuances of these threats and implementing proactive measures.
Robust access controls and monitoring systems are foundational elements in thwarting insider threats, while security awareness training empowers developers to recognize and respond effectively to potential risks.
While the role of technology, including encryption and multi-factor authentication, cannot be overstated in safeguarding against evolving threats, it’s crucial to adopt a holistic approach that addresses both technical and human factors, fostering a culture of security consciousness and collective responsibility.
Looking for more ways to improve Java security?
Since you made it to the end of the article, it’s safe to say that you’re committed to improving Java security — MergeBase is, too!
One of the biggest advantages of the Java ecosystem is the strength of its libraries and frameworks, but that doesn’t mean they’re faultless. MergeBase’s complete software security solution can help you secure your Java environment and safeguard your applications, reducing the burden on your dev team.
Contact MergeBase to learn more, or start your free 14-day trial today.

