Choosing the best software composition analysis tool is an important decision that will affect your cybersecurity for years to come. But since the product category is relatively new, it can be difficult to evaluate your options and understand what sets the best solutions apart.
We put together this comparison guide to help you choose the right tool based on the most important criteria. This guide is based on our extensive industry experience, conversations with cybersecurity professionals, and our own research. It compares four of the top SCA tools using a five-point scoring system in five key areas.
In this buyer’s guide, we address the following:
Software Composition Analysis: What it is and What it does
Software composition analysis (SCA) is a category of tools that detect vulnerabilities within the components of your software offerings. This protects you from inheriting third-party vulnerabilities from the open source libraries you’ve built your product on and licensed third-party code you’ve incorporated into your product.
Top SCA tools bring you a host of benefits, including:
- ✓ Timely notifications of third-party vulnerabilities in your code
- ✓ Support for patching those vulnerabilities
- ✓ Reduced time wasted on false positives
- ✓ Higher morale on your IT security and development teams (especially if you can reduce false positives)
- ✓ Better protection against embarrassing data breaches
- ✓ A high-value, high-security offering for your customers
Choosing the right SCA tool is a win for your product, your customers, your employees, and your shareholders.
Why choosing the right SCA tool is so important
Open source software continues to be routinely exploited by cybercriminals, and it’s one of the top sources of data breaches today. Notable examples include the infamous breach at Equifax in 2017 and the 2021 Log4J exploit. The threat is so great that the U.S. Department of Homeland Security published an alert in 2020 that political adversaries are continuously targeting these vulnerabilities.
As the threat grows, the need for tools to protect against it grows too.
“Growing risks and ubiquitous use of open-source software in development make software composition analysis essential to cyber security. Security and risk management leaders must expand the scope of tools to include detection of malicious code, operational and supply chain risks.” —Gartner®
If you want to protect your software supply chain from these threats, you need a software composition analysis solution.
And it needs to be a good one. Because while choosing the best SCA tool brings you all the benefits, choosing a lackluster SCA tool comes with several dangers of its own:
- ·Missing key vulnerabilities leaves you, your product, and potentially your customers exposed to cyber criminals.
- · An abundance of false positives eats into your developers’ time, raising the total cost of ownership of the solution to begin with.
- · Inferior SCA tools have a high false positive rate, which our survey found increases vulnerability fatigue, erodes employee morale, and damages relationships between IT and dev teams.
Choosing the right SCA tool is vital—but with this evolving threat landscape, what essential criteria do you need to consider for your SCA? If you already have an SCA, are you certain the features are still effective?
The Best Software Composition Analysis tools on the market today
MergeBase is a premium SCA solution, but we’re not the only option. To give you an overview of the best SCA tools and help you choose which one is right for you, we’ve examined the most high-functioning, feature-rich SCA suites in the category: Snyk, BlackDuck (by Synopsis), and Mend.
MergeBase
MergeBase is a purpose-built full featured SCA tool. The only SCA tool that includes Runtime Protection. MergeBase was founded by a team of longtime cybersecurity developers to address the most pressing issues that companies face when protecting themselves from third-party vulnerabilities.
Snyk
Snyk develops security analysis tools designed to find, fix and monitor known threats in open source code. Their solution emerged from developer-friendly tools.
BlackDuck (by Synopsis)
Synopsis’s SCA solution, Black Duck, has been in the application security space the longest at over 15 years. It added security capabilities in 2015, having previously been focused on license compliance.
Mend (formerly WhiteSource)
Mend offers agile open source security and license compliance management. They integrate with the DevOps pipeline to detect open source libraries with security or compliance issues.
The Best SCA tools: a side-by-side comparison
We’ve measured these tools’ competencies (as well as our own) in the five most critical areas where a quality SCA tool needs to perform.
We’ll unpack these individual competencies in a moment, but here’s how these tools stack up against each other at a glance on a scale of 1–5. These scores are based on each tool’s capabilities as of October 2022.
This scoring system rates the best SCA tools across five key competencies:
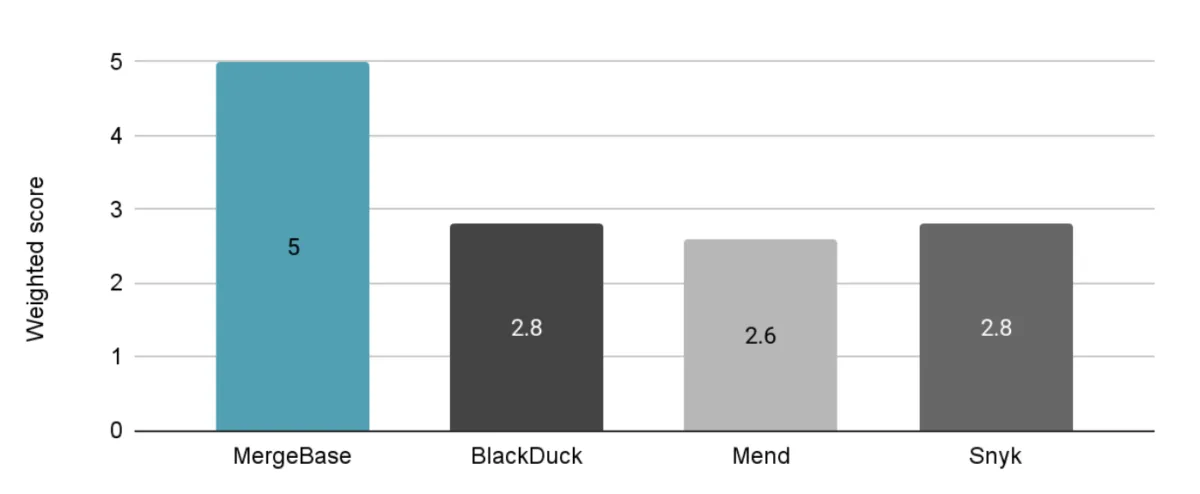
“Wait. MergeBase just gave themselves a perfect rating? That’s pretty suspect.”
Fair point, but there’s a good reason for this. Well, actually, there are four:
- This scoring system focuses on the five areas that are absolutely vital to choosing a strong SCA solution. We arrived at these factors after countless conversations with IT security and development teams over the years: these are the ones that come up over and over.
- We could score all of these solutions across many more factors—like the size of the company’s internal research team, the number of integrations available, etc. However, getting reliable numbers for these factors is difficult to do, and even if we did get accurate numbers, they could change next week.
- The whole reason we started MergeBase was to master these five areas. When companies switch from one of these other players to MergeBase, it’s because of one (or several) of these factors.
- While MergeBase is strictly an SCA solution, these other SCA tools are parts of much larger software security suites. With a breadth of coverage comes a lack of focus. If we were to rate ourselves against everything that Mend does, our score would look a lot different—but we’re not playing their game.
But now you must be wondering: how do these solutions stack up on these five factors individually?
Developer guidance with a compatibility check
It’s no secret that developers play a crucial role in securing your software supply chain, but most SCA solutions do not make their jobs any easier. After an SCA identifies a vulnerability, only a handful of solutions provide usable developer guidance on how to patch it.
Unfortunately, technology organizations have discovered that most developer guidance requires the developer to invest more time to research. But even after that research, you still don’t know whether the patch will break your application. In a 2021 IBM Security™ study, 59% of respondents cited delays associated with patching vulnerabilities as a reason their organizations hadn’t become more resilient to cyber threats. In other words, vulnerabilities were known—but the patches just weren’t applied.
When selecting an SCA, you need a solution with advanced developer guidance, a precise compatibility check, and suppression management, empowering your developers to find the best upgrade path instantly.
How each tool performs in the area of developer guidance
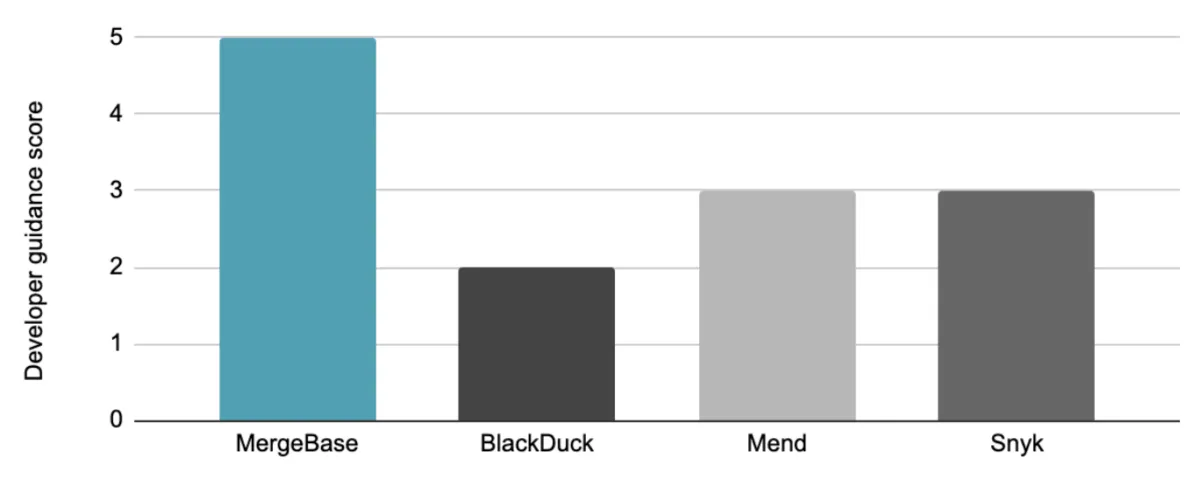
We graded these tools’ developer guidance capabilities on the following five-point scale:
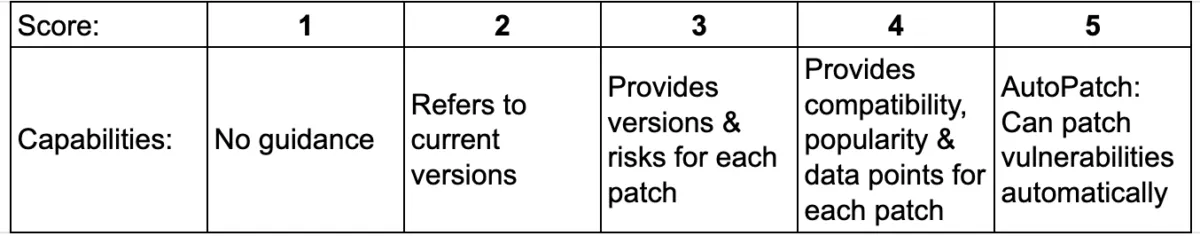
The MergeBase advantage: Not only does our tool provide information on each patch’s risks, compatibility, and popularity, but MergeBase can automatically implement safe patches for you—so your product and security teams can make informed decisions and move on.
Comprehensive SBOM support
The software bill of materials (SBOM) plays an essential role for both software companies and their enterprise customers. Organizations that deliver software applications face increasing regulatory and compliance pressures to produce a comprehensive SBOM: one that not only shows vulnerabilities and licenses but also points out technical debt (portions of code that need future cleanup).
For enterprise customers, it’s more common to ask your vendor for an accompanying software bill of materials. But it’s also important to validate the SBOMs that these vendors provide—which an advanced SCA tool can help you do.
How each tool performs in the area of SBOM support
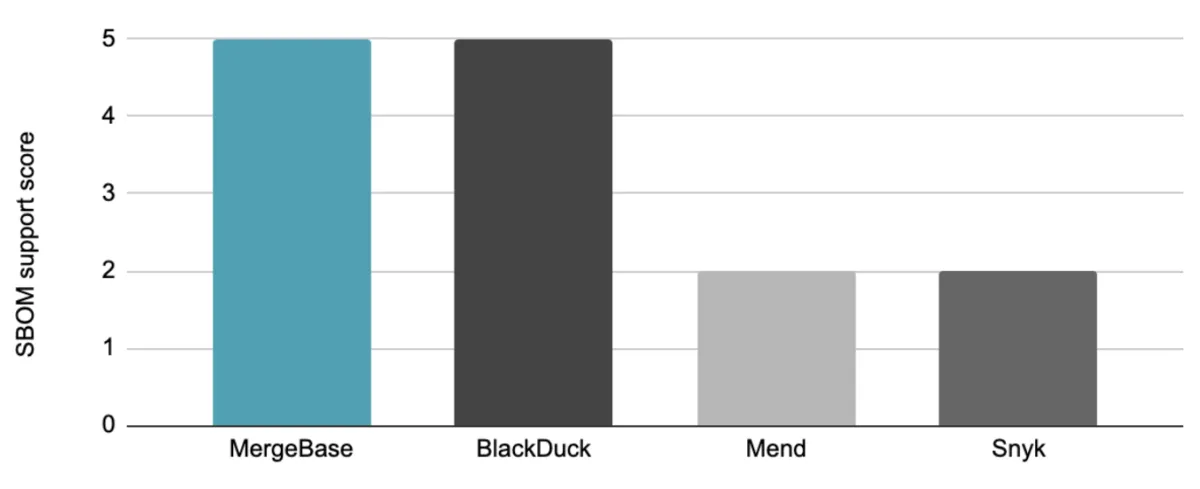
We graded these tools’ SBOM support on the following five-point scale:
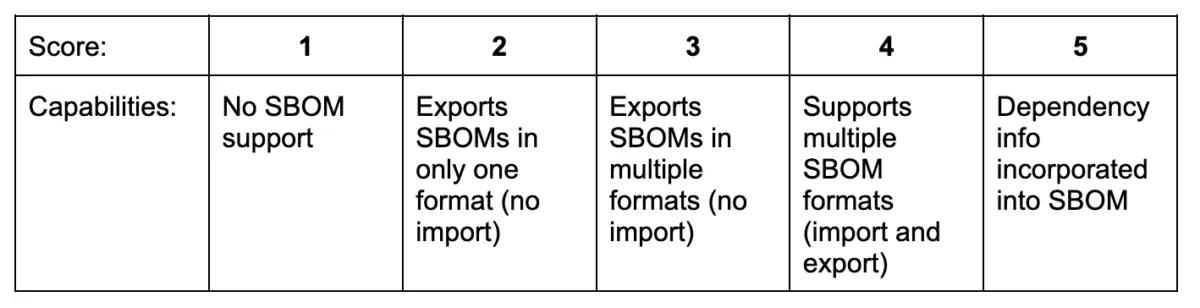
The MergeBase advantage: MergeBase allows you to import and export multiple SBOM formats, and it clearly delineates all dependency relationships between the components and subcomponents in your application. (Plus, you can visually navigate your SBOM inside MergeBase, so you can see how your third-party code is nested and where any given vulnerability lies.)
Low false positives output
SCA false positives are just plain bad for business. In our 2022 report, The True Costs of False Positives in Software Security, 62.1% of surveyed technology leaders revealed that decreasing false positives is a higher business priority than increasing true positives.
No organization has an abundance of developers on hand to help fix application vulnerabilities. False positives waste valuable time and significantly hamper productivity on both development and security teams—and they can harm relationships between teams.
Every false positive is a technical wild goose chase. So when you’re considering an SCA solution, you don’t just want it to catch all the real vulnerabilities—you also want it to have a low false positive rate.
How each tool performs in the area of accuracy
We ran each of these tools against a set of applications with 511 known vulnerabilities to see how many they’d catch, how many they’d miss, and how many false positives they’d flag. Here’s how they stacked up:
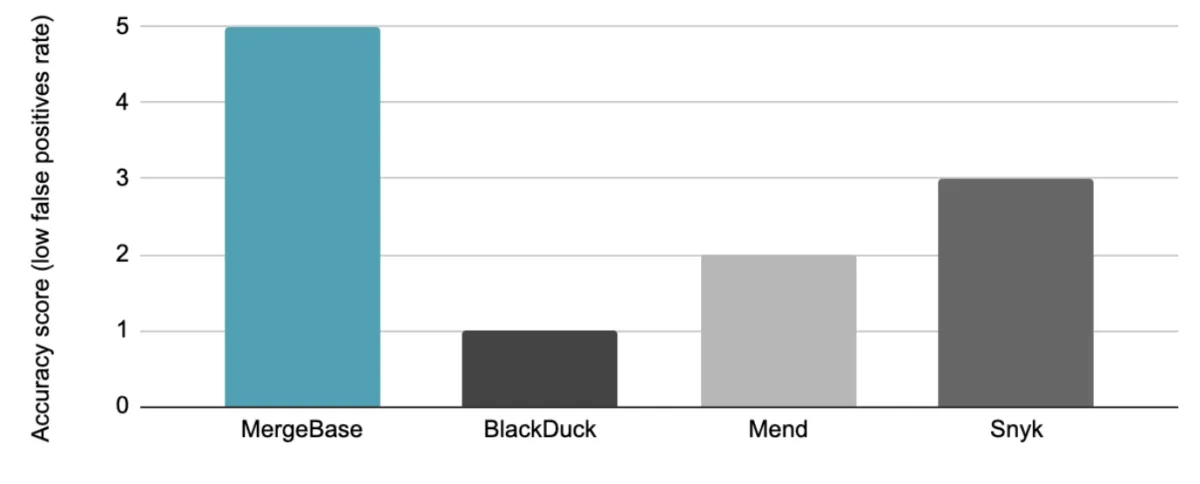
We graded these tools’ accuracy on the following five-point scale:

The MergeBase advantage: One of the reasons we built MergeBase was to take on the problem of false positives in the SCA space—without missing true positives. By design, MergeBase is the most accurate SCA tool on the market today.
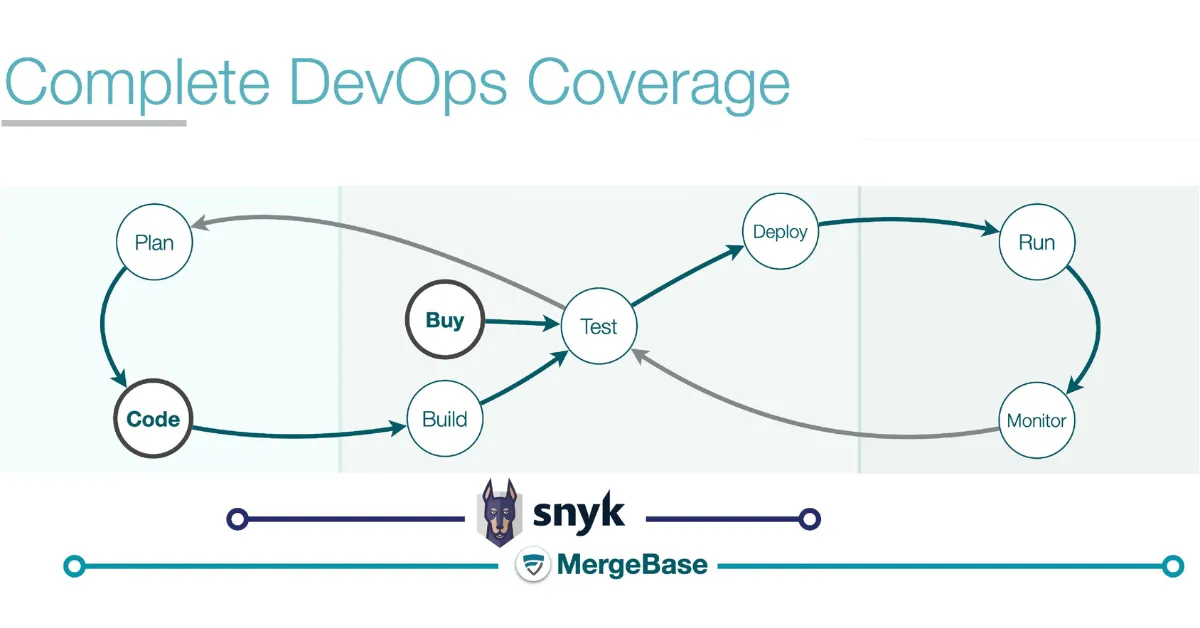
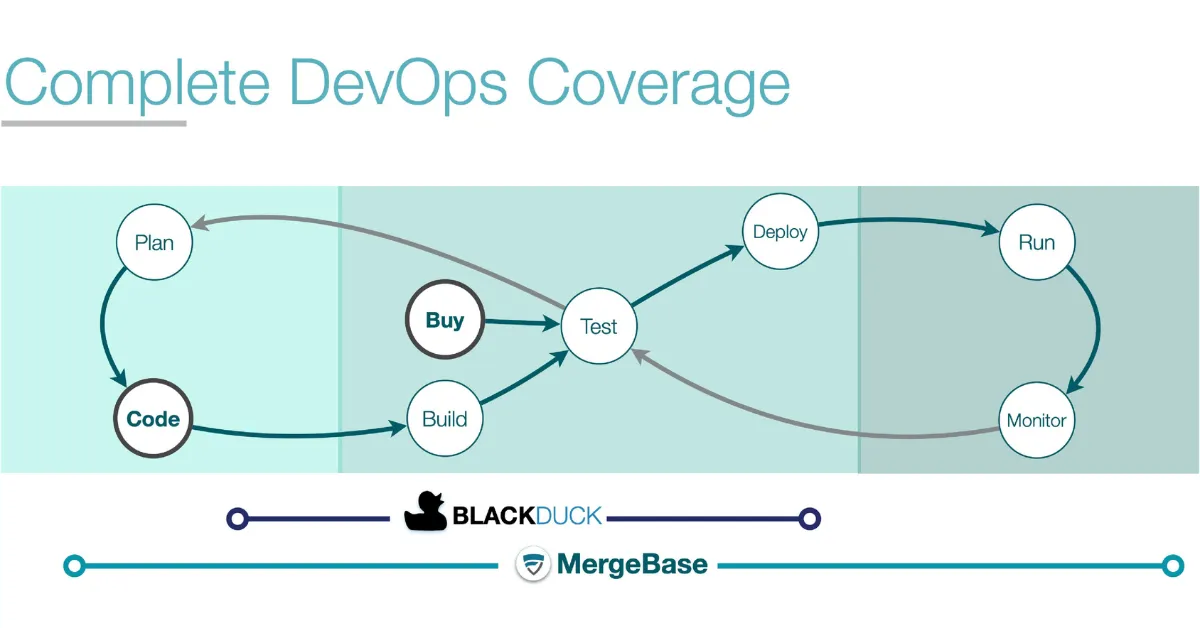
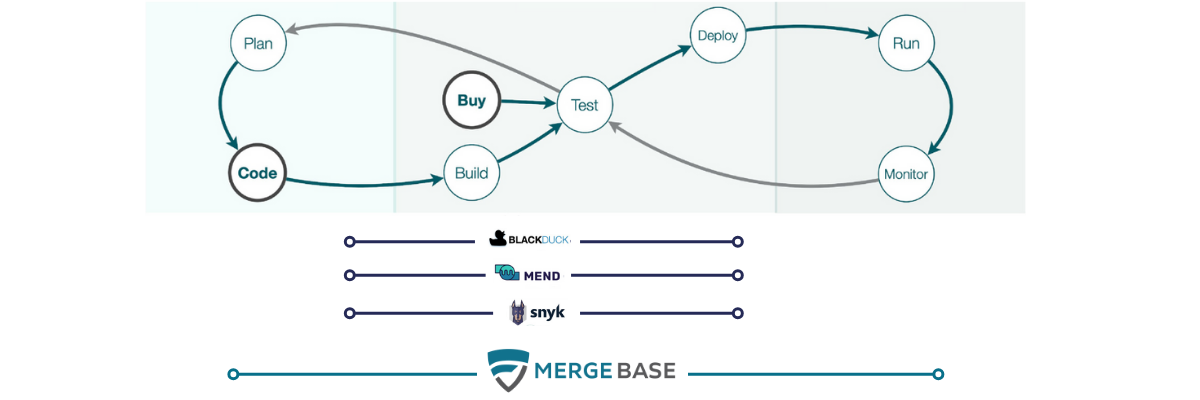
Integration to the DevOps process with runtime protection
We found that most SCA solutions claim to protect and integrate into your entire DevOps process. Each of these leading tools integrates with your build pipeline and repository and supports container scanning.
However, most tools leave one critical area unprotected: running applications. If your SCA tool provides runtime protection, you gain deeper insight into vulnerabilities of all your running applications, enabling more effective prioritization.
When comparing SCA tools, look for solutions that integrate entirely into your DevOps process, with comprehensive runtime protection that gives you the most effective remediation options to protect your applications.
How each tool performs in the area of DevOps integration
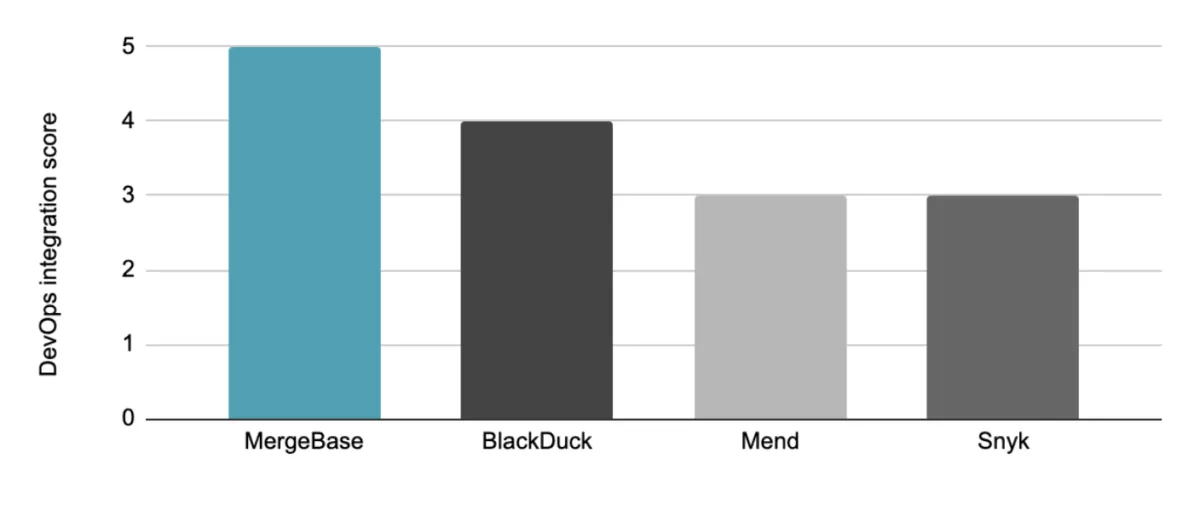
We graded these tools’ DevOps integration capabilities on the following five-point scale:
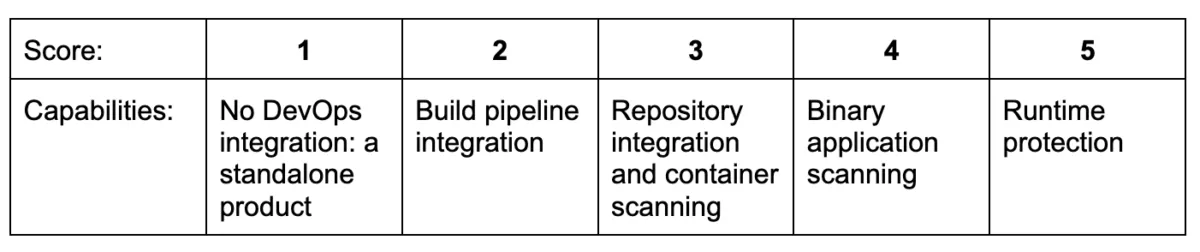
The MergeBase advantage: MergeBase is built on a Shift Left Security philosophy. Our SCA tool protects your build pipeline and runtime, integrates with your repository, and allows for both container and binary scanning—so you’re always aware of known vulnerabilities in your third-party code, whether it’s open source or licensed.
Total cost of ownership
And then, of course, each SCA tool comes with a cost. This should go beyond the price you pay for the tool, though: you should also consider how much labor it will cost you to use the tool.
This incorporates a few of the factors we’ve already visited. A tool with a high false positive rate is going to eat up your developer’s time. Likewise, the less developer guidance a tool provides, the more time your team has to spend figuring out how to respond to vulnerability alerts.
Then there’s the pricing structure itself to consider. Some SCAs are transparent with pricing, others use complex formulas based on variable directional metrics, and others are entirely opaque. Furthermore, some SCA tool subscriptions come with hidden fees and limitations—which means you could end up paying a great deal more than the original purchase price.
So when considering SCA options, look for two things:
- Competitive pricing: Find a vendor that uses transparent, straightforward pricing
- Labor savings: Choose a tool with robust enough capabilities to reduce the labor costs associated with third-party vulnerability protection
How each tool performs in the area of total cost of ownership
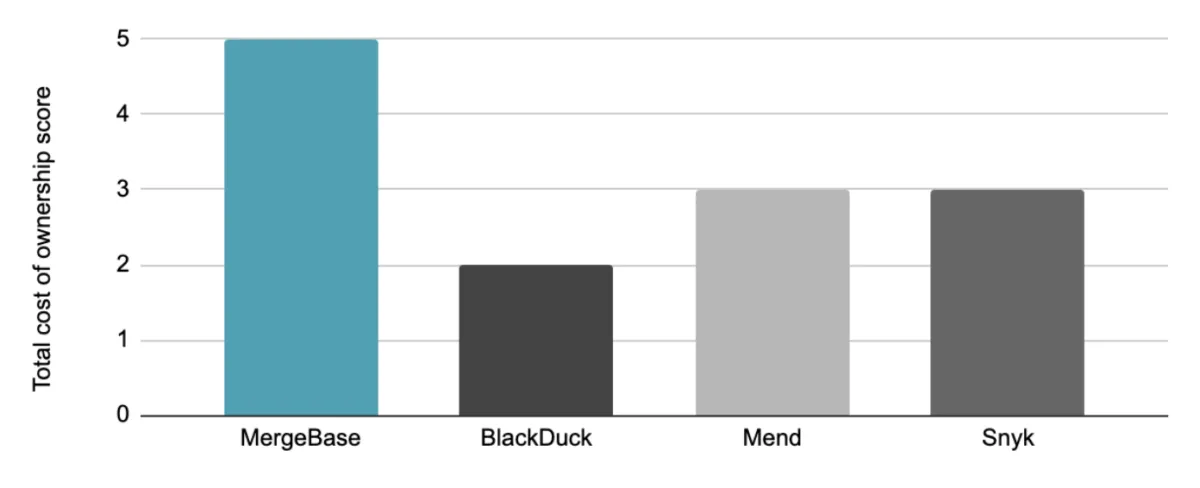
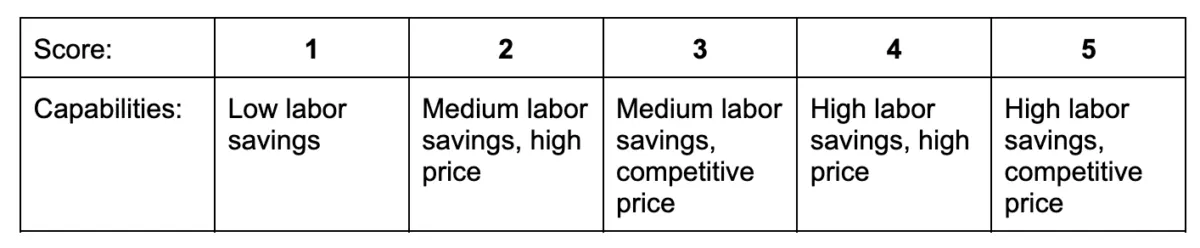
We graded these tools’ total cost of ownership on the following five-point scale:
The MergeBase advantage: Our pricing model is entirely transparent, with no hidden fees or limits—plus MergeBase saves labor with a low false positive rate, clear developer guidance, automatic patching, prioritization, and other remediation options.
Conclusion
Selecting the right SCA is critical to protecting your organization, and these five factors are the strongest indicators of how valuable an SCA tool can be to your organization.
We built MergeBase so that you can rapidly secure your software supply chain without slowing down your business. If you’re considering SCA options, you’re welcome to download our comparison worksheet to build your own SCA benchmark for your organization.
If you’re exploring SCA options and still aren’t convinced, or if you’d like to delve even deeper into comprehensive analyses, continue reading these following pages:
- · MergeBase and Sonatype
- · Black Duck vs. WhiteSource (now Mend) vs. MergeBase
- · Snyk vs. Black Duck vs. MergeBase
- · Snyk vs. WhiteSource (now Mend) vs. MergeBase
For more information on this guide and to learn more about how MergeBase can help protect your software supply chain, please connect with us at info@mergebase.com. Or, if you’d like to see MergeBase in action, we’d love to show you a demo!