Component Detail Reference
Risks Tab
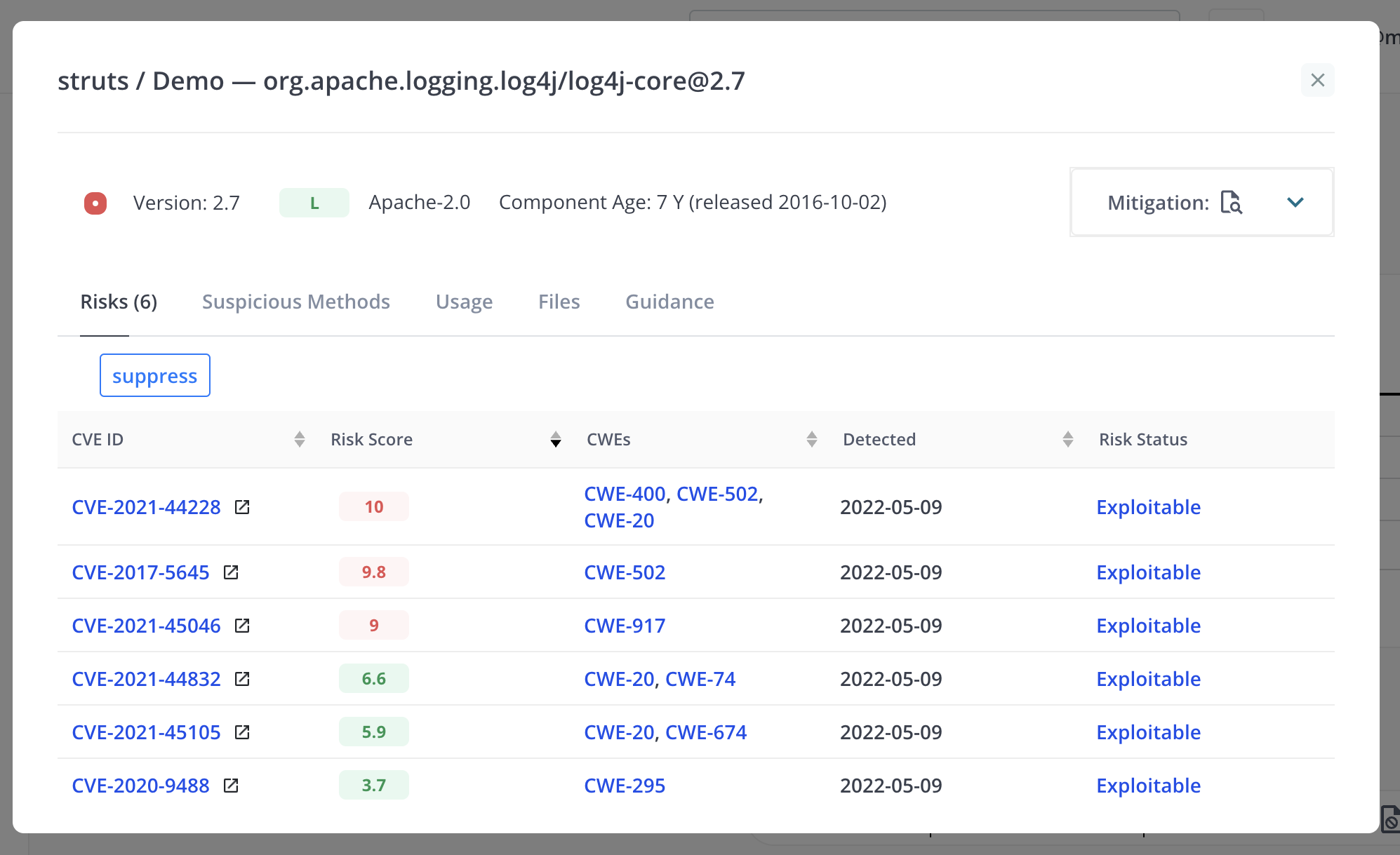
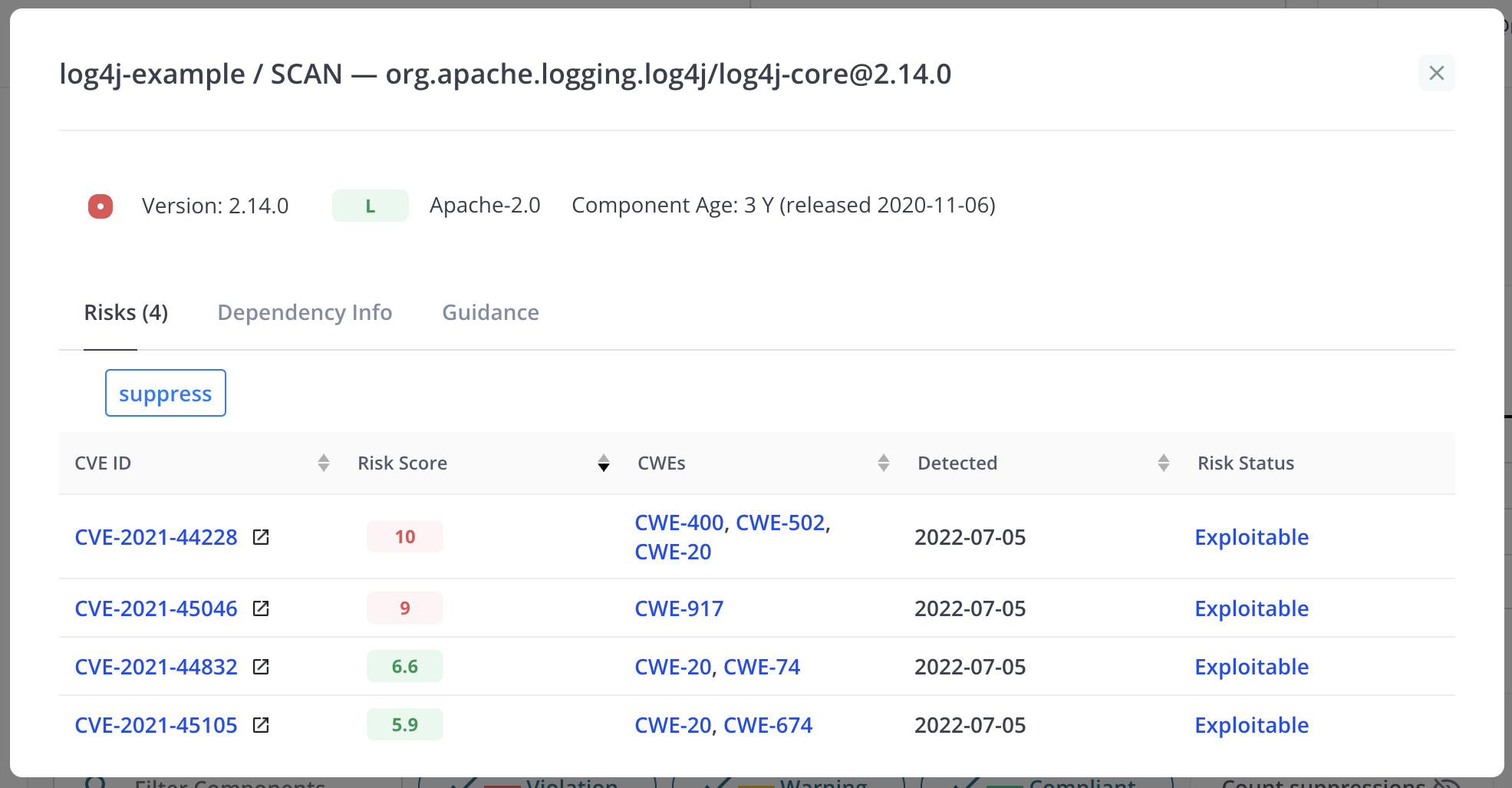
For vulnerabilities sourced from the NVD database, the risks view provides a link to the complete vulnerability description at nvd.nist.gov (opens in a new window). This view also provides controls to accept risks for specific vulnerabilities. If a risk is accepted, the user must provide a reason. Once a risk has been accepted, the vulnerability counts displayed in other views will be adjusted accordingly.
The user can also suppress all the risks for the component using the “suppress” button, which works the same way as the “suppress” button in the Application Detail view. If the component is already suppressed, the “suppress” button is replaced with “remove” and “edit” buttons.
Dependency Info
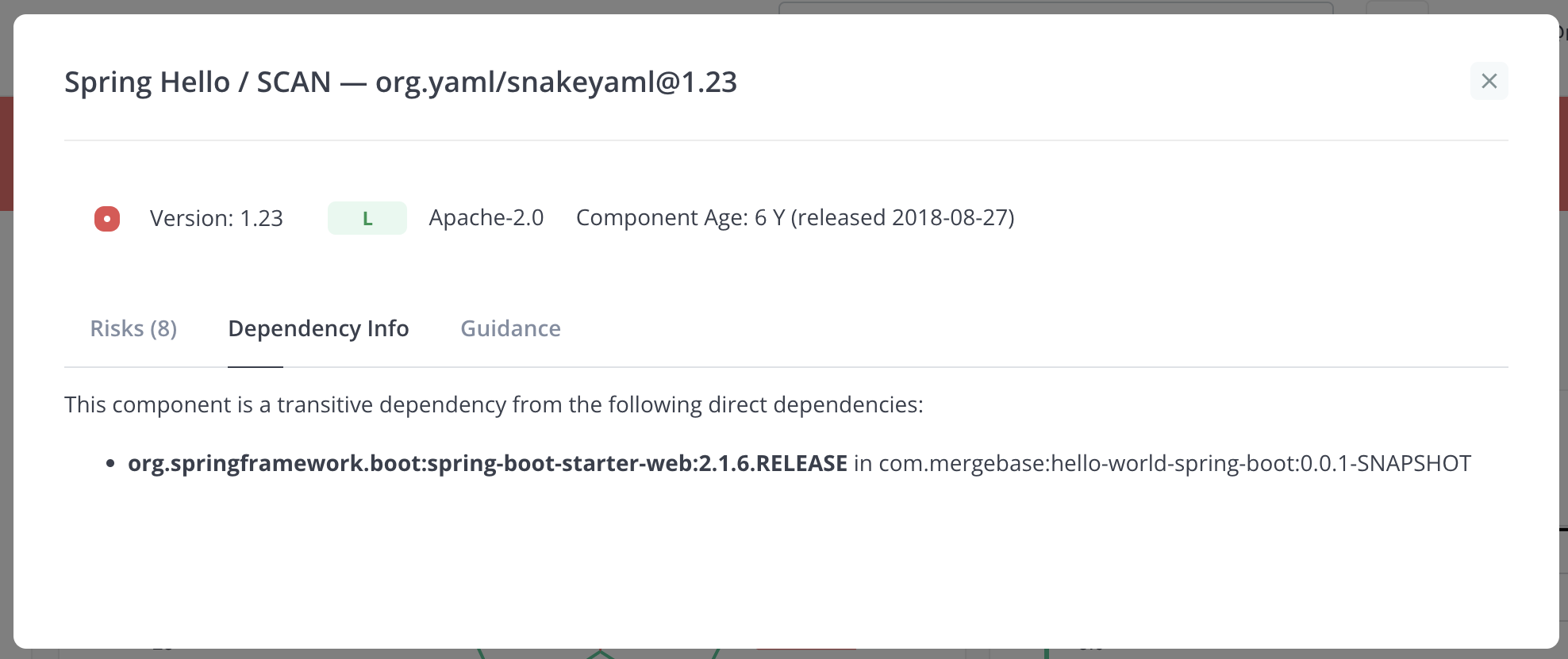
This tab shows whether the component is included in the application as a direct dependency or if it is included because it is a transitive dependency. For Java applications using Maven, the information includes the pom.xml file that contains the direct dependency and, if the component version is managed, the location of the dependency management.
Guidance
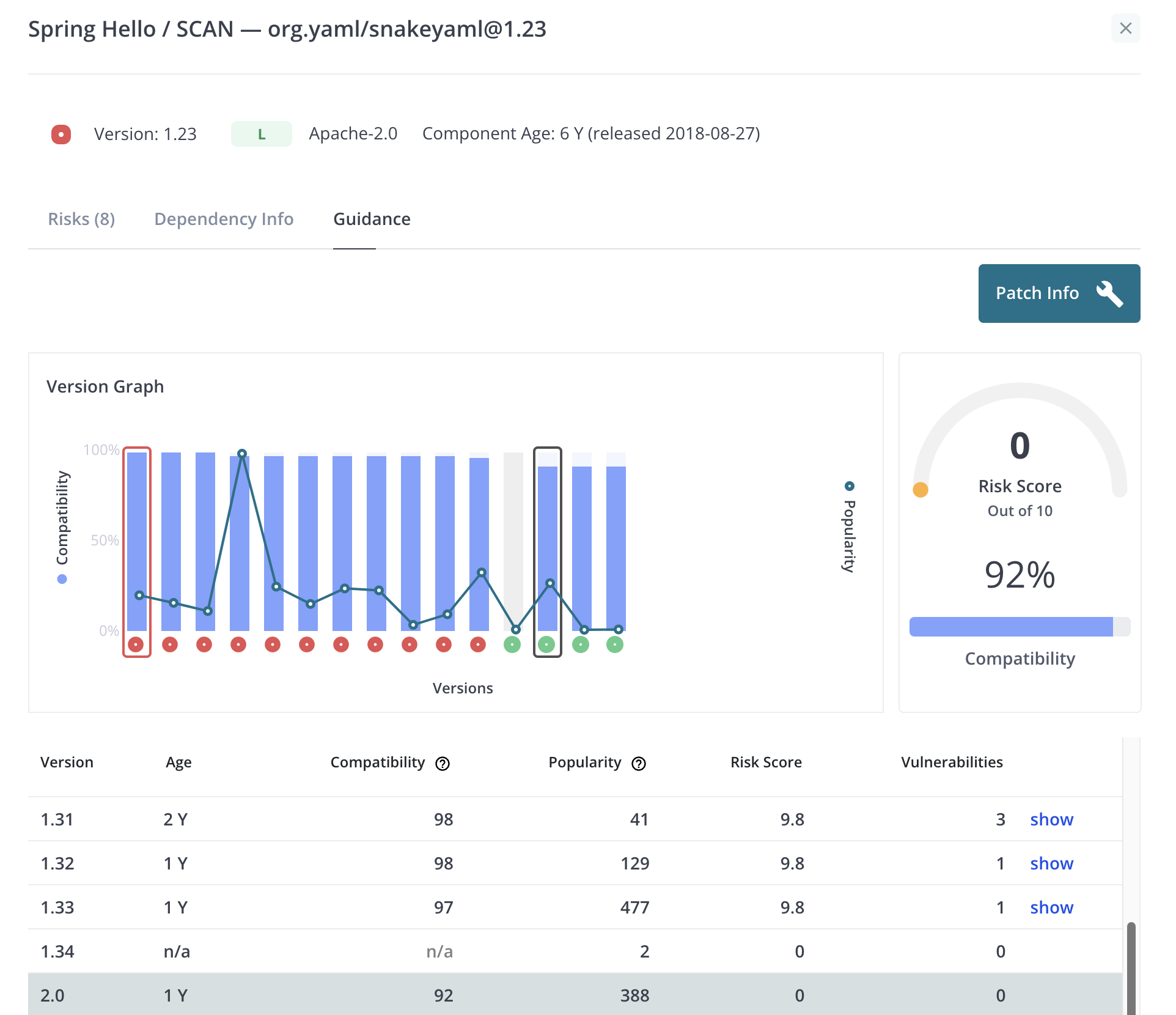
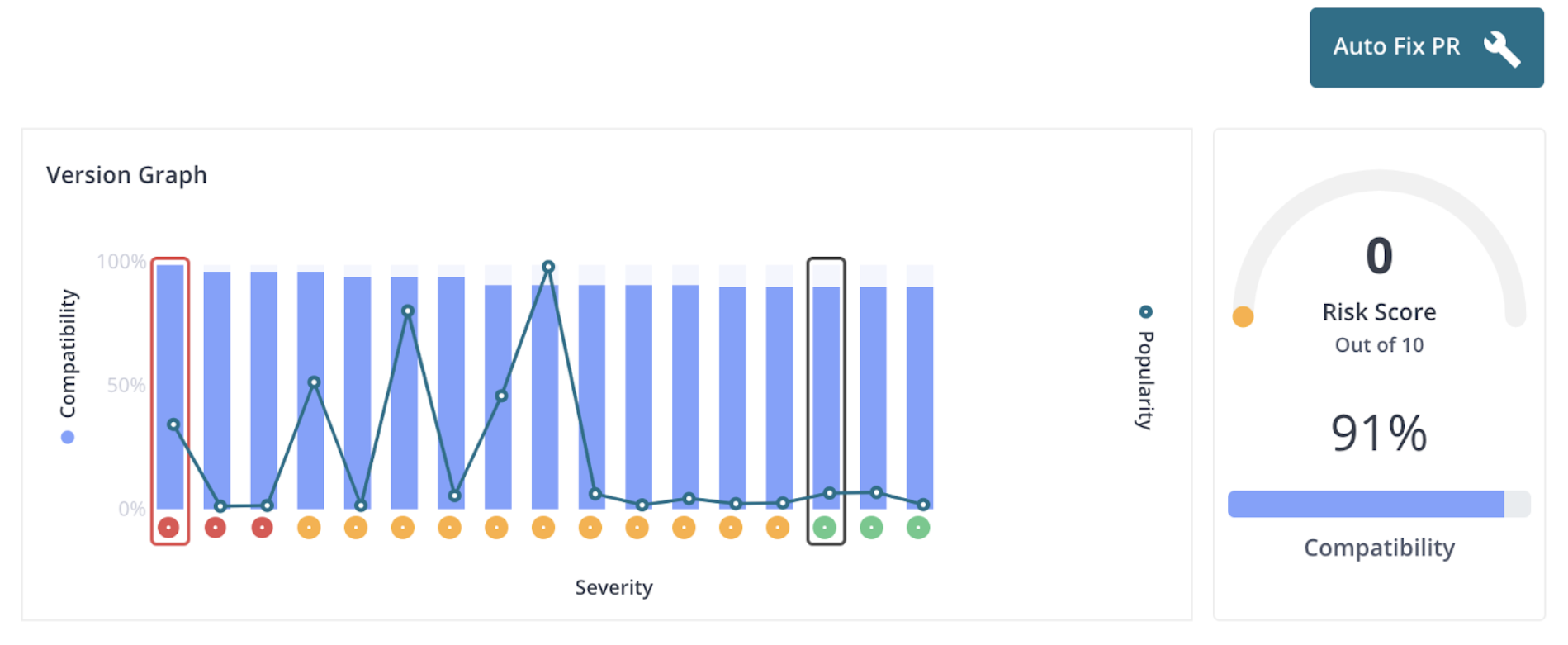
This tab provides information on potential upgrades. The user is presented with a chart showing versions that follow the current version. Below the chart is a table with information about each version. The user can click on a bar to scroll the table to the selected version. The popularity score is based on the number of open source projects that currently use that version of the component. The compatibility score is based on the difference in the public API of the current version versus the selected version. The user can click on the vulnerability count to expand the row to show all the vulnerabilities associated with that version (if any).
Patch Info
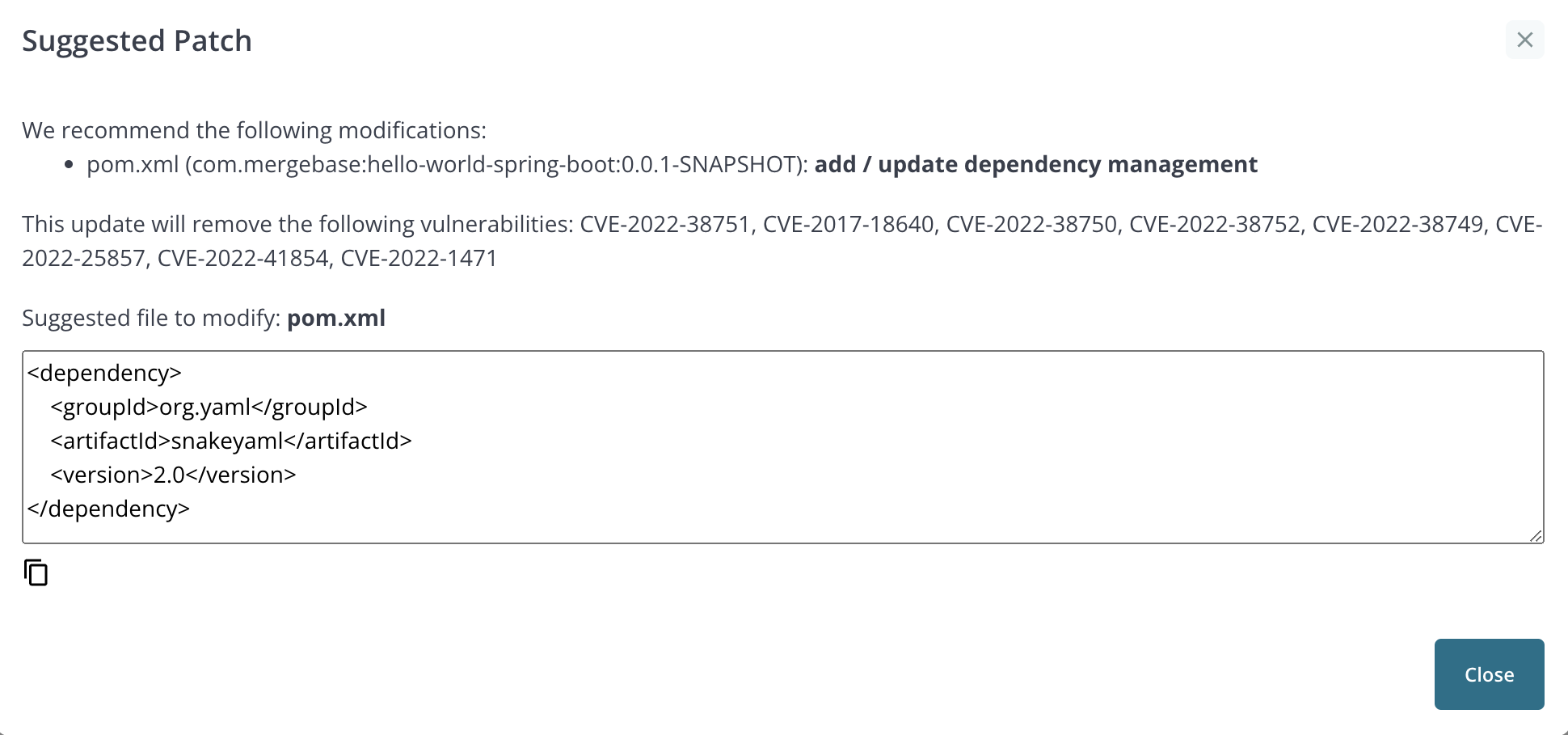
In addition to scrolling the table, clicking on a bar will enable the “Patch Info” button. Clicking on the button will display a window with information to upgrade the component.
Auto Fix Pull Requests (Maven only)
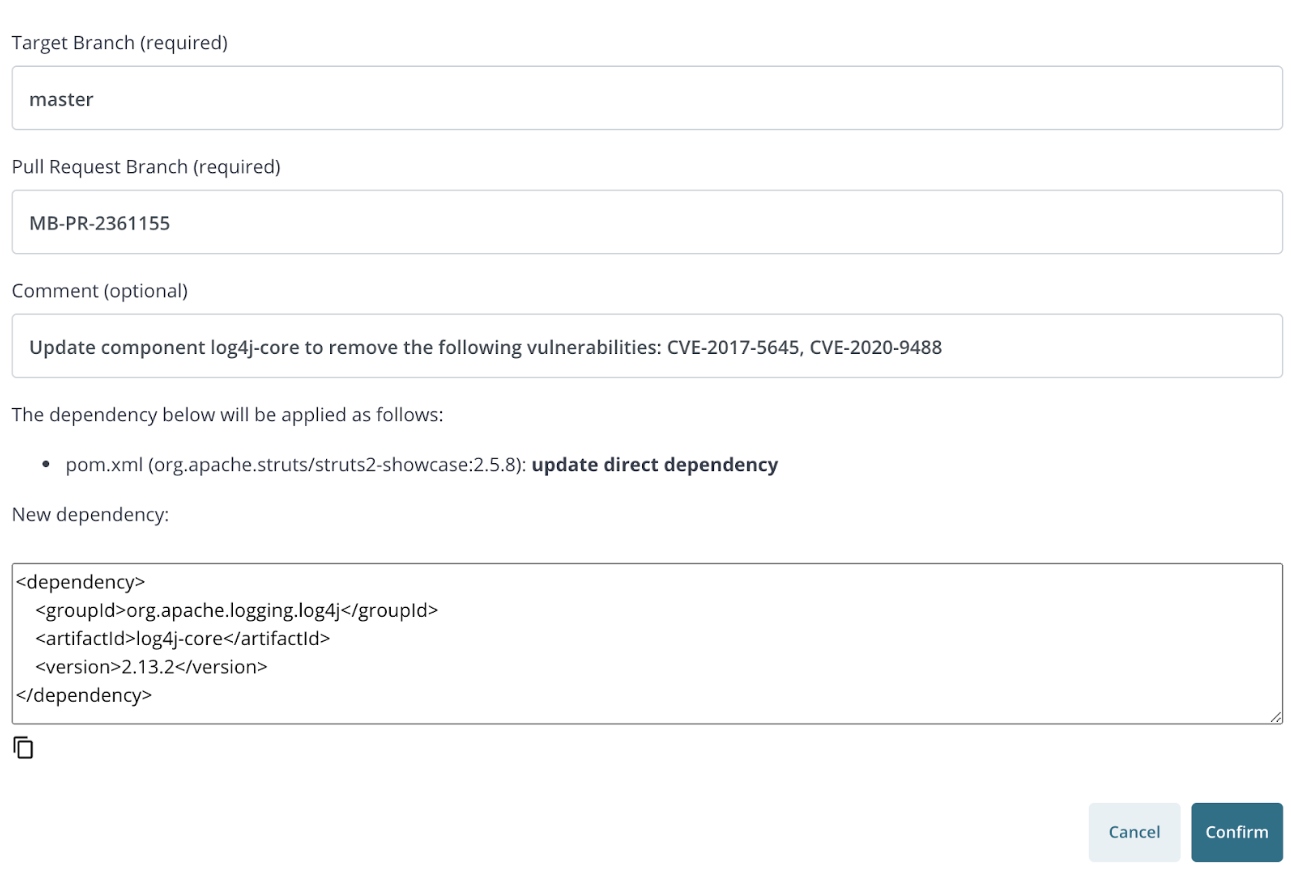
If GitHub integration is enabled and the source scan is from a Maven project in GitHub, the “Patch Info” button is replaced with an “Auto Fix PR” button.
Clicking on the button opens a dialog that will allow the user to create a pull request to upgrade the component.
Component Detail - Binary Scans and Inoculated Applications
For binary scans as well as inoculated applications, different information is presented in the Component Detail view.
As with source scans, the component detail includes the release date and the “suppress” button. There is also a drop down menu to set a mitigation on the component (e.g. block or monitor).
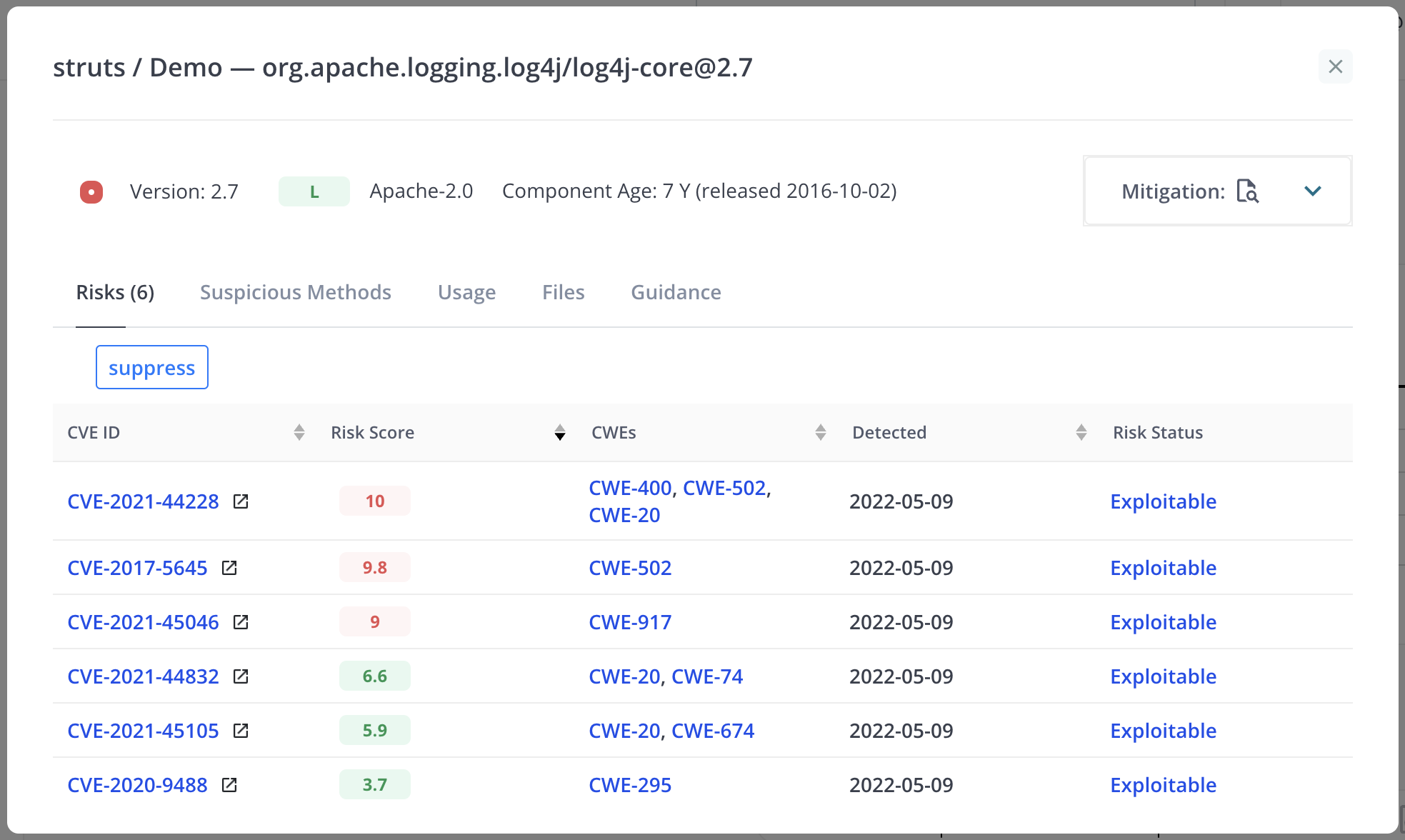
The Risks and Guidance tabs are the same as for source scans. However, the Guidance tab will not display an “Auto Fix PR” button even if GitHub integration is enabled. This is because scans from jar files do not contain the git repository information required to create the patches and pull requests. There is also no information about dependencies.
Suspicious Methods
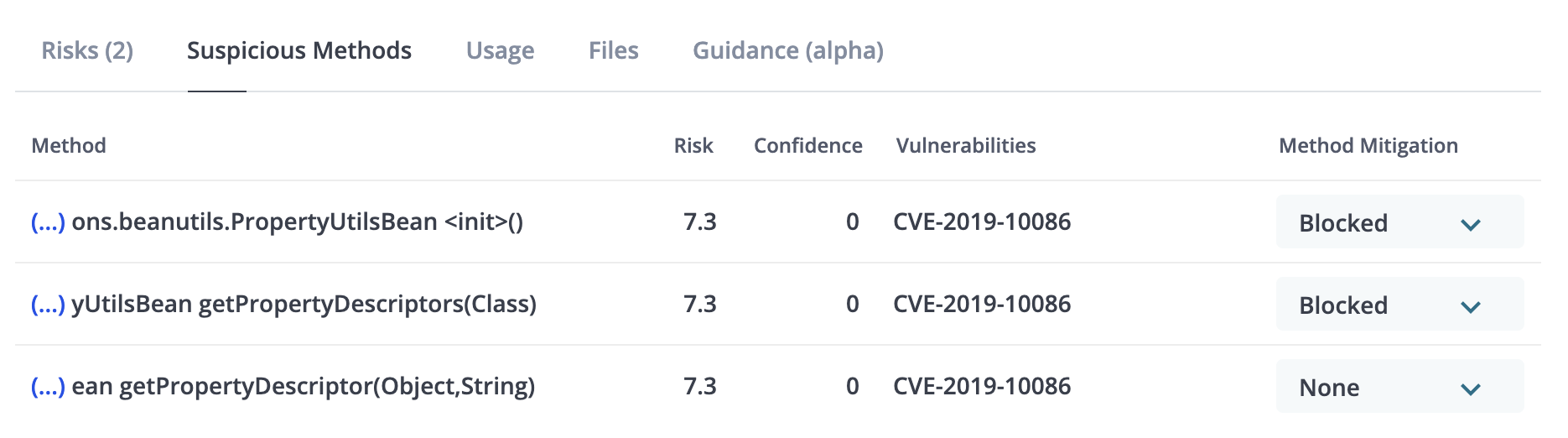
Suspicious methods are methods identified by MergeBase as being implicated in an exploit for the identified vulnerabilities. The MergeBase user can choose to block or monitor the individual methods displayed in this list.
Usage
If monitoring has been enabled at the component or suspicious method level, the information collected will be displayed here.
Files
This tab will display the file path(s) associated with the component when it was scanned.